Touchpad Computer Book Class 8 Ch 4 Solution
Computer Safety and Security
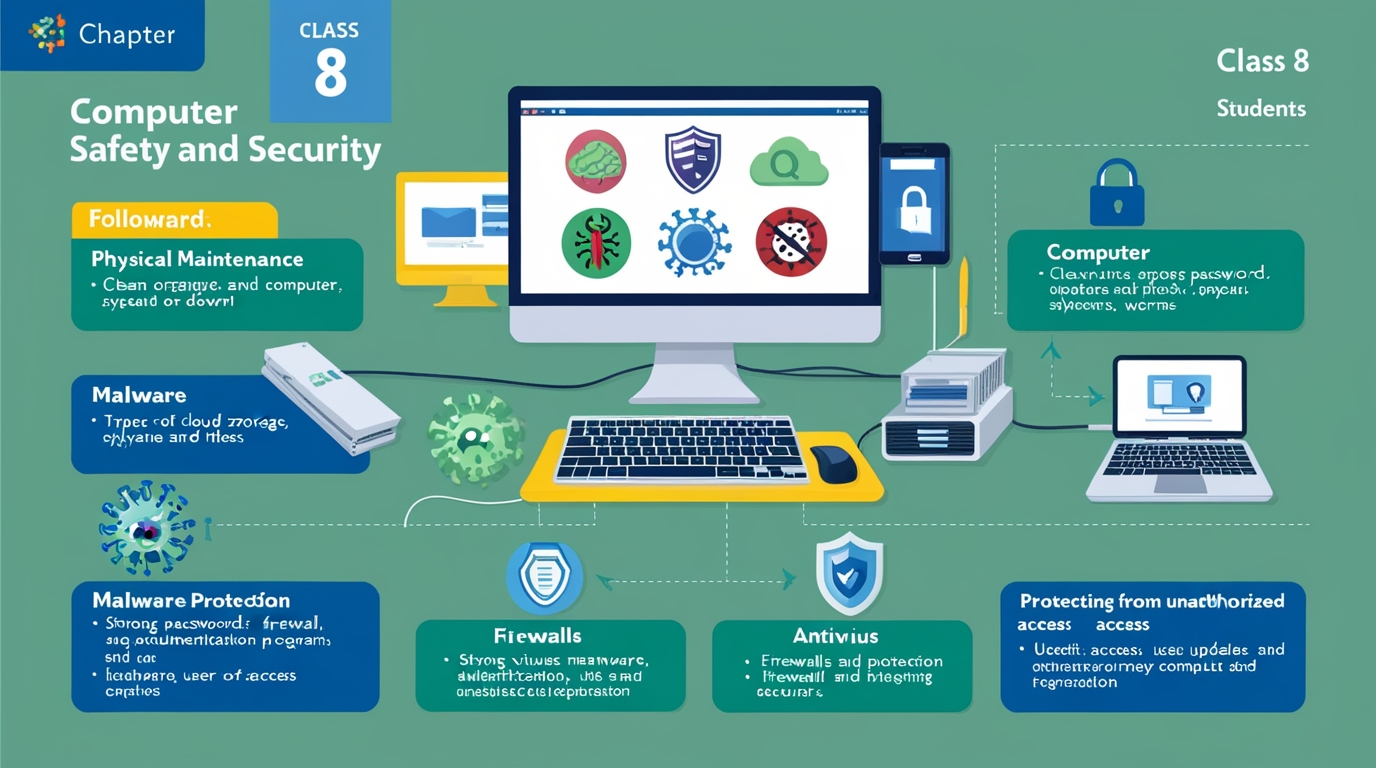
Chapter Overview: Computer Safety and Security
The chapter “Computer Safety and Security” in the Touchpad Computer Book for Class 8 covers essential practices and tools to protect computers and data from harm. In today’s digital environment, maintaining a secure computer is vital for safeguarding sensitive information and preventing unauthorized access. This chapter introduces students to various concepts and tools designed to keep computers secure and operational. Below are some of the main subtopics covered in this chapter:
How to Keep Your Computer Physically Fit:
Physical maintenance is essential for the longevity and performance of computers. This includes keeping the computer clean, ensuring it has proper ventilation, avoiding eating or drinking near it, and regular hardware inspections.How to Backup Your Important Files:
Backing up important files protects against data loss due to system failures, accidental deletion, or malware attacks. Backup options include external hard drives, cloud storage, and automated backup software to ensure data is secure and recoverable.Understanding Malware:
Malware is any software intentionally designed to harm or exploit a computer. Common types of malware include viruses, trojans, spyware, ransomware, and worms. Recognizing malware and knowing how to defend against it is critical for computer security.Firewall:
A firewall acts as a barrier between a computer and potential threats from the internet. It monitors incoming and outgoing network traffic and blocks unauthorized access, enhancing the security of connected devices.Protecting Your Computer from Illegal Access:
To prevent unauthorized access, various measures can be taken, such as using strong passwords, enabling multi-factor authentication, and setting up user access controls. This ensures only authorized users can access sensitive information.Other Maintenance Techniques:
Regular maintenance practices like defragmenting the hard drive, updating software, and deleting temporary files can help improve system performance and prevent slowdowns.Antivirus Software:
Antivirus programs are essential for detecting, blocking, and removing malware. They provide real-time protection against cyber threats and keep the system clean by scanning and removing harmful files.
Below are the solutions to the exercises in Touchpad Computer Book Class 8 Ch 4: Computer Safety and Security, which reinforce these key concepts.
Touchpad Computer Book Class 8 Ch 4 Solution : Exercise Solutions
1. Multiple Choice Questions (Tick ✓ the correct option)
a. Norton is a/an:
- (i) System Software
- (ii) Operating System
- (iii) Antivirus ✓
- (iv) All of these
b. You can backup your data into:
- (i) UPS
- (ii) External Hard Drive ✓
- (iii) Mouse
- (iv) None of these
c. _____ is a type of malware.
- (i) Encryption
- (ii) Trojan Horse ✓
- (iii) AVG
- (iv) None of these
2. Fill in the Blanks Using the Words Given Below
- biometric, malware, encryption, decryption, zombie
a. Malicious software is known as malware.
b. Recognition of biological characteristics is an example of biometric authentication.
c. Encryption is the process of converting data into a readable form.
d. Decryption is the opposite of encryption.
e. Zombie works in a similar way as the spyware.
This exercise in the Touchpad Computer Book Class 8 Ch 4 Solution introduces key cybersecurity terms, helping students understand core concepts like biometric authentication, encryption, and decryption.
3. Short Answer Type Questions
a. What is meant by authentication? What are the types of authentication?
Answer: Authentication is the process of verifying a user’s identity before granting him or her
access to a computer system.
Types of authentication include:
- Password-based authentication
- Biometric authentication (such as fingerprint or facial recognition)
- Two-factor authentication (2FA)
b. What is a trojan?
Answer: Trojan horse is a type of malware. It conceals itself inside the software that seems legitimate.
c. What is the use of an antivirus program?
Answer: An antivirus program is used to detect the presence of a virus on a computer and remove
the virus.
By answering these questions, students can grasp basic concepts around authentication, trojans, and the role of antivirus software, crucial topics in Touchpad Computer Book Class 8 Ch 4 Solution.
4. Long Answer Type Questions
a. How will you keep your computer physically fit?
Answer:
- Regularly clean the computer components, such as the screen, keyboard, and mouse.
- Ensure proper ventilation around the computer to avoid overheating.
- Keep food and drinks away from the computer to prevent spills and damage.
- Check for loose connections and ensure all hardware is securely in place.
b. What is malware? How does it affect your computer? Mention some types of malware.
Answer:
- Malware is malicious software that harms or exploits a computer system.
- It can slow down the computer, steal data, delete files, or make the system inoperable.
- Types of malware include viruses, trojans, spyware, ransomware, and worms.
c. Differentiate between virus and worm.
Answer:
- A virus attaches itself to a legitimate program and spreads when the program is executed, often causing damage to files or system functions.
- A worm is a standalone malware that replicates itself across networks without needing to attach to a host program, causing network congestion or system overload.
These long-answer responses in the Touchpad Computer Book Class 8 Ch 4 Solution help deepen understanding of malware, physical computer maintenance, and the differences between viruses and worms.
Let’s Solve
Guess my name.
a. My name resembles a micro organism. My prime motive is not to cause damage but to clone myself on the host system.
Answer: Virusb. I specialize in concealing myself. Though, I belong to the cyber world, my name has its roots in Greek mythology.
Answer: Trojanc. I do not collect information from the computer. I wait for the hacker to give me commands.
Answer: Zombie
Application-based questions.
a. Manisha wants to prevent other people from accessing her computer without permission. Which security measure would help her in this situation?
Answer: Password protectionb. Nitin is working on some important data. If he modifies the data, then he won’t be able to use the original data. The original data would be required for future use. What can he do with the data to make sure that the original data is preserved?
Answer: Take a backup of the original data.c. Anuj is working on his computer. Suddenly, the computer slows down, and some unwanted files appear automatically. Help him to identify the problem with his computer and suggest a way to resolve the problem.
Answer: His computer is infected by a virus. It can be resolved by installing antivirus software like McAfee.
Let’s Explore
- Question: Surf the internet to find the latest antivirus and protective measures you can use to secure your computer.
Answer: Do it yourself.
Let’s Get Better
- Question: Do you think it is acceptable to steal other people’s information? Discuss with your class.
Answer: This is a discussion-based question. Answer with personal or classroom opinions.
Tech Practice
Question: Surf the internet and learn the process of taking the backup of data.
Answer: Do it yourself.Question: Learn how to choose the password for your email account.
Answer: Do it yourself.
Additional Information
- Concept-Based Questions:
a. Question: Authentication is the process of verifying a user’s identity before granting him or her access to a computer system. Types of authentication Are: Password Protection, Biometric Authentication, etc.
Answer: Explanation provided in the question itself.b. Question: What is a Trojan horse?
Answer: A Trojan horse is a type of malware. It conceals itself inside software that seems legitimate.c. Question: What is an antivirus program used for?
Answer: An antivirus program is used to detect the presence of a virus on a computer and remove the virus.d. Question: List ways to physically clean your computer.
- Cleaning the keyboard
- Cleaning the mouse
- Cleaning the monitor
Answer: The answer is in the list provided above.
e. Question: What is malware, and what are its types?
Answer: Malware is malicious software designed to damage or carry out other unwanted actions on a computer system. Types of malware include viruses, worms, trojan horses, spyware, zombies, ransomware, rootkits, and backdoors.f. Question: What is the difference between a computer virus and a computer worm?
Answer: A computer virus is a piece of code or program developed to corrupt data or program files on a computer system. It enters the computer without the user’s permission, and the user may not even realize that the computer is affected.- A computer worm is a type of malware that can replicate itself without human interaction. It consumes a lot of memory space in replication. Once a computer is infected by a worm, its processing speed slows down, works unexpectedly, and may halt other tasks.
Conclusion
The Touchpad Computer Book Class 8 Ch 4 Solution on Computer Safety and Security provides students with essential knowledge about protecting computers from threats and maintaining their physical health. By understanding concepts like malware, backups, firewalls, and antivirus programs, students can build a solid foundation in computer security. These skills are indispensable in the digital age, where protecting data and devices is crucial for safe and responsible technology use.
This solution is useful for the students of the CBSE and HBSE boards.
Visit vacancyconnect.com regularly for more valuable & Real Information.